Introduction to Intel VT-rp
文章目录
1. Material
- SPEC:ISE
- Hypervisor-managed Linear Address Translation by Chao Gao slides
- Hypervisor-managed Linear Address Translation by Chao Gao video
2. Background
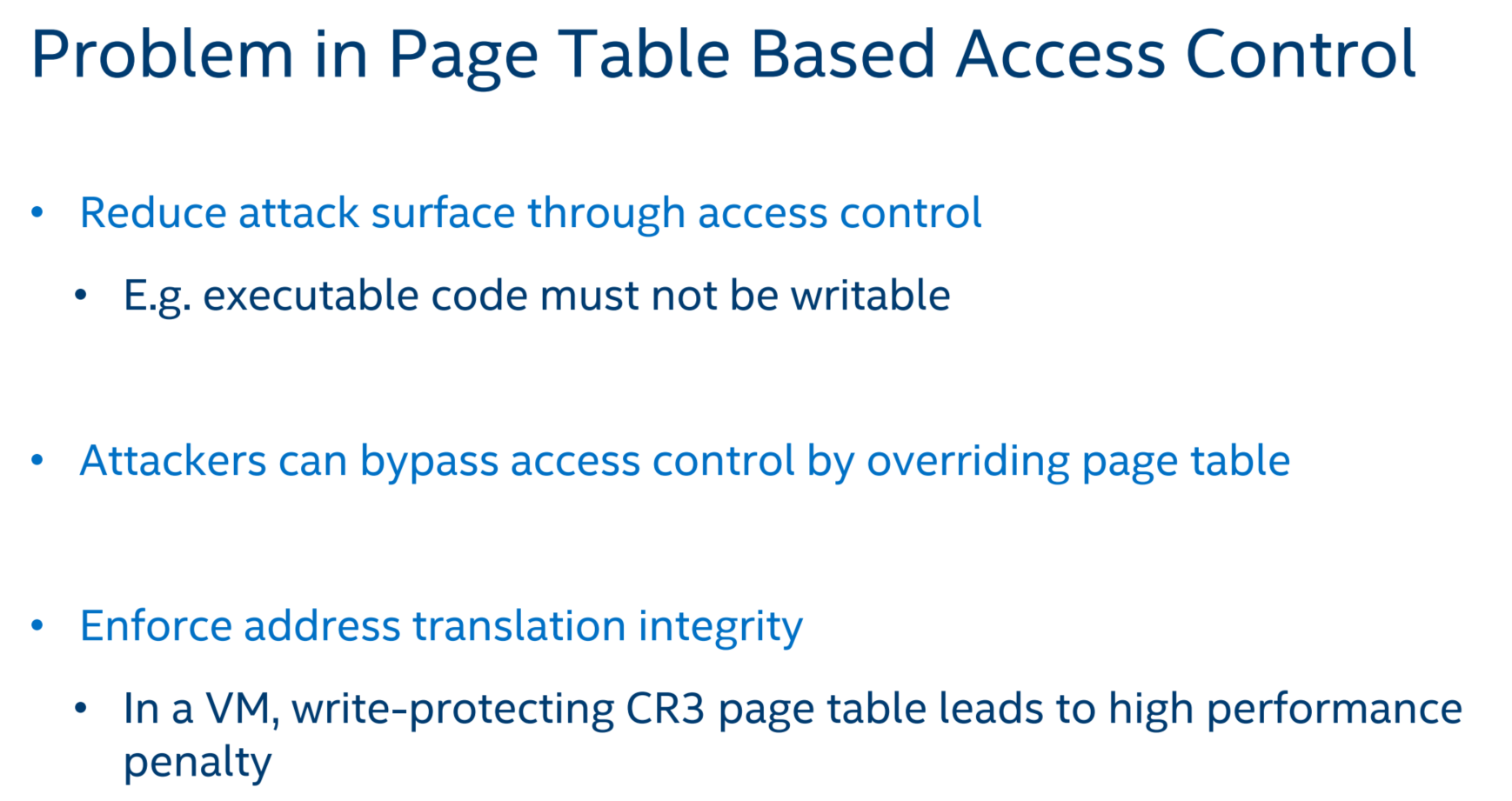
对于write-protecting CR3 page table leads to high performance penalty的解释如下:
VMMs could enforce the integrity of these specific guest linear to guest physical mappings (paging structures) by using legacy EPT permissions to mark the guest physical memory containing the relevant guest paging structures as read-only. The intent of marking these guest paging structures as read-only is to ensure an invalid mapping is not created by guest software. However, such page-table edit control techniques are known to cause very high overheads(EPT violation VM Exit) due to the requirement that the VMM must monitor all paging contexts created by the (Guest) operating system.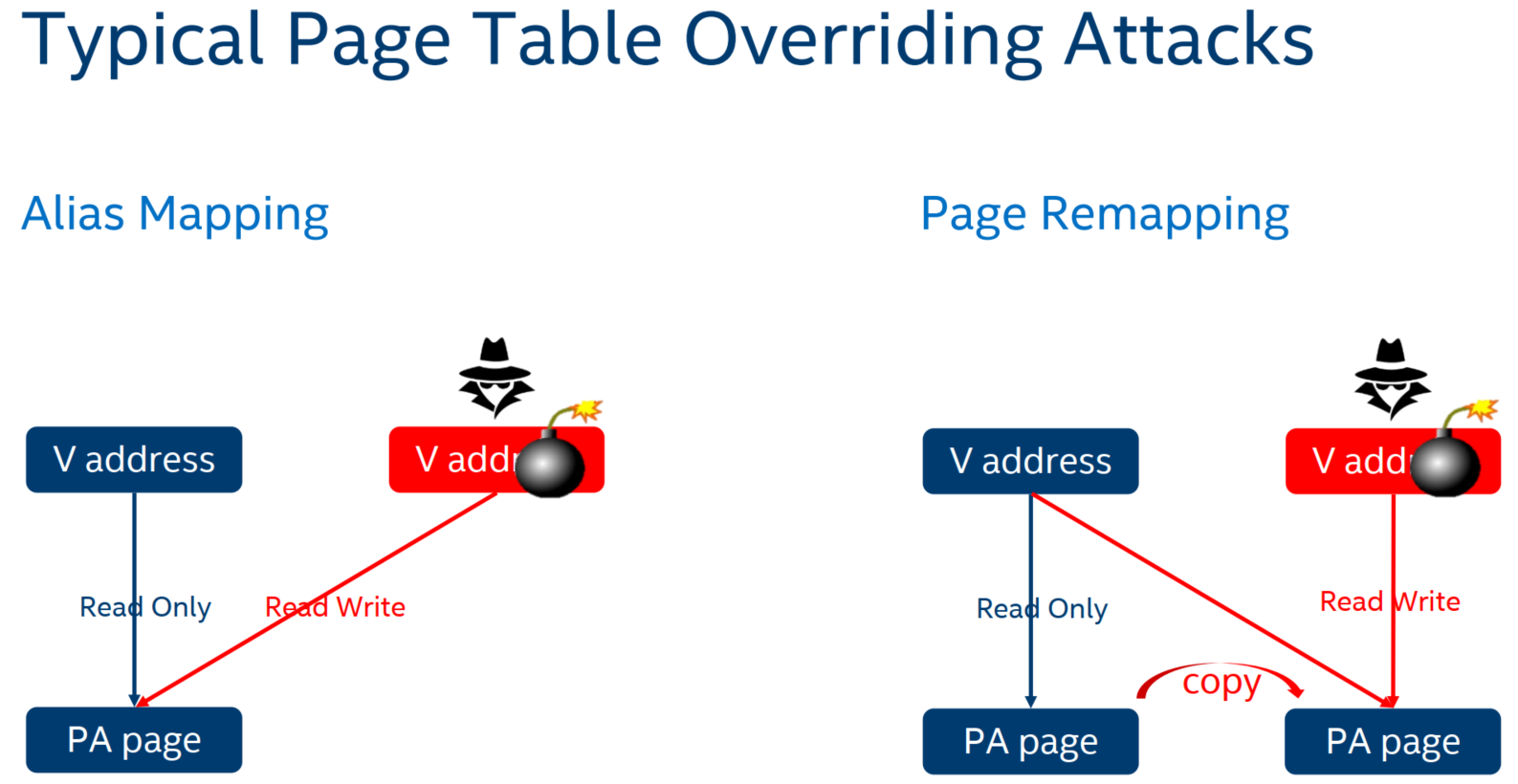
3. Terms
- Intel VT-rp(Intel Virtualization Technology - Redirect Protection)
- HLAT(Hypervisor-managed Linear Address Translation)
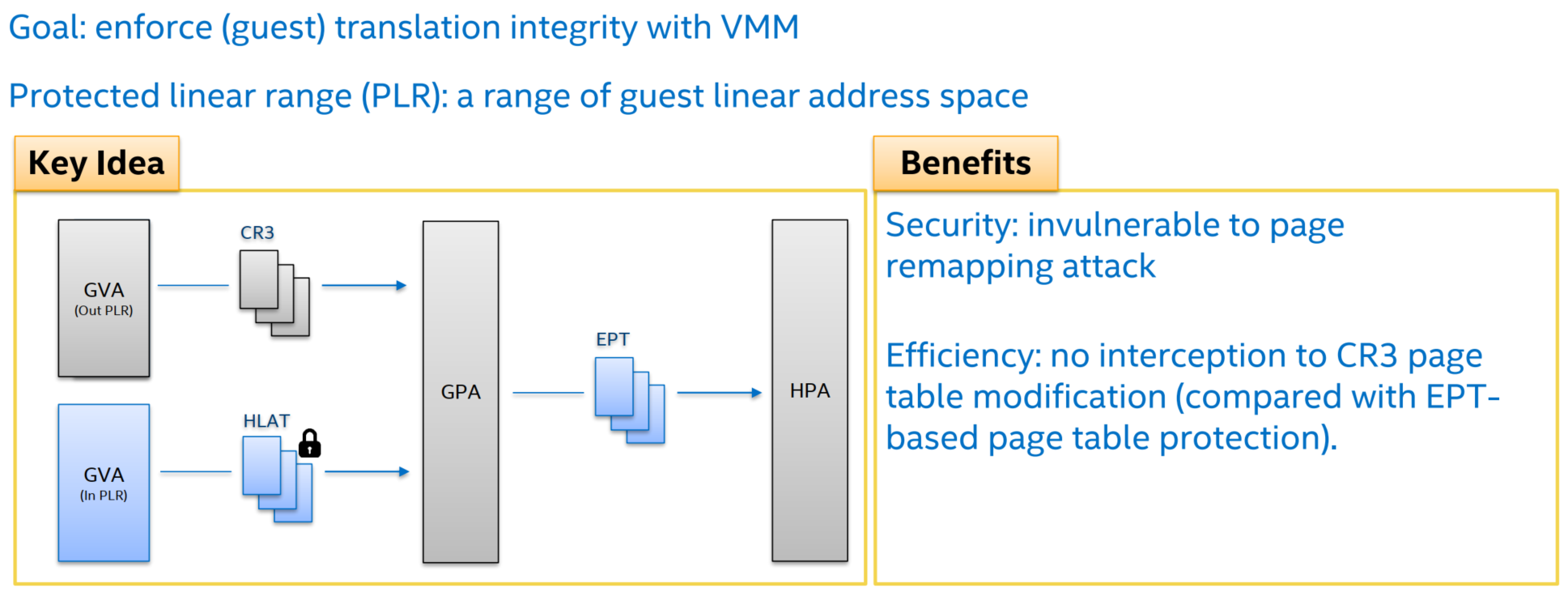
- PLR(Protected Linear Range)
- PW(Paging Write)
- VPW(Verify Paging-Write)
4. VT-rp

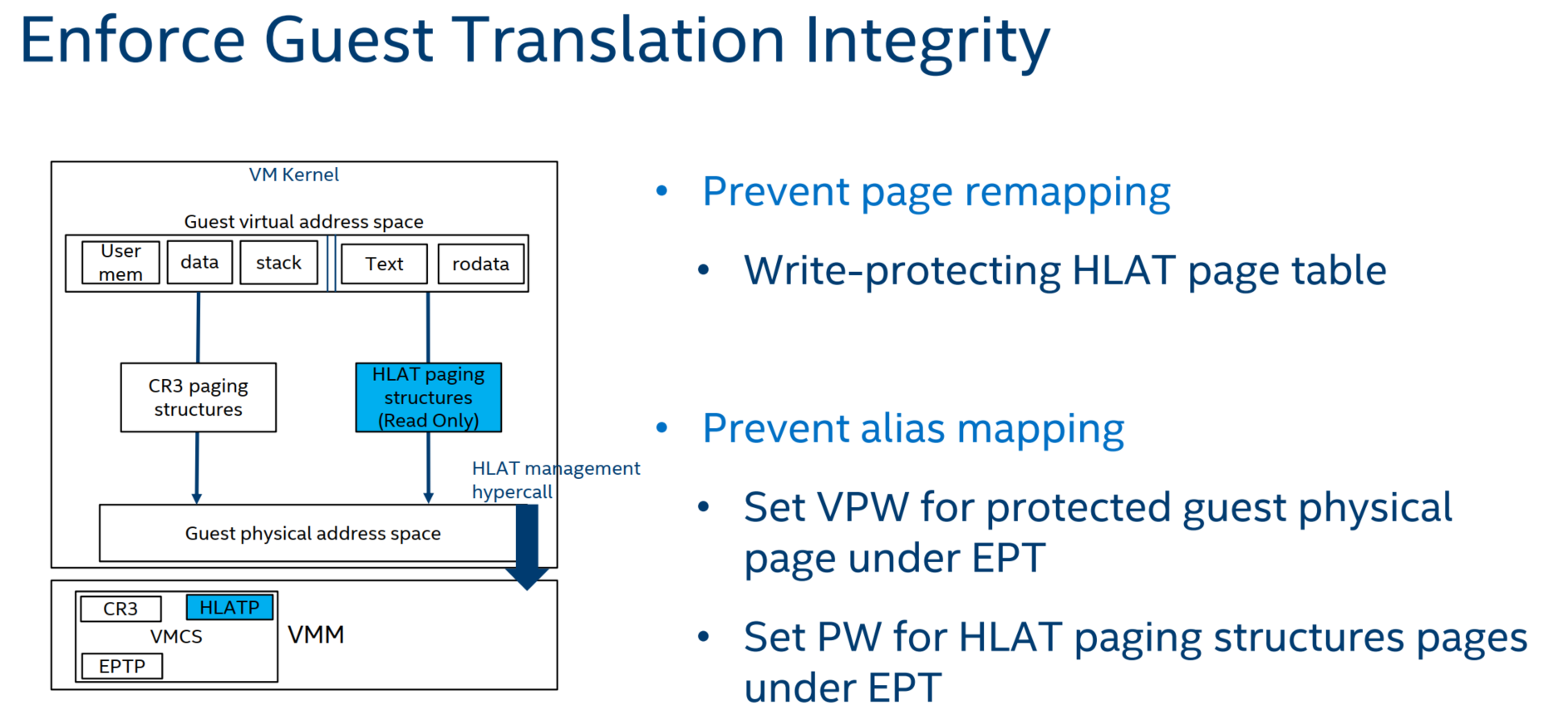
4.1 HLAT
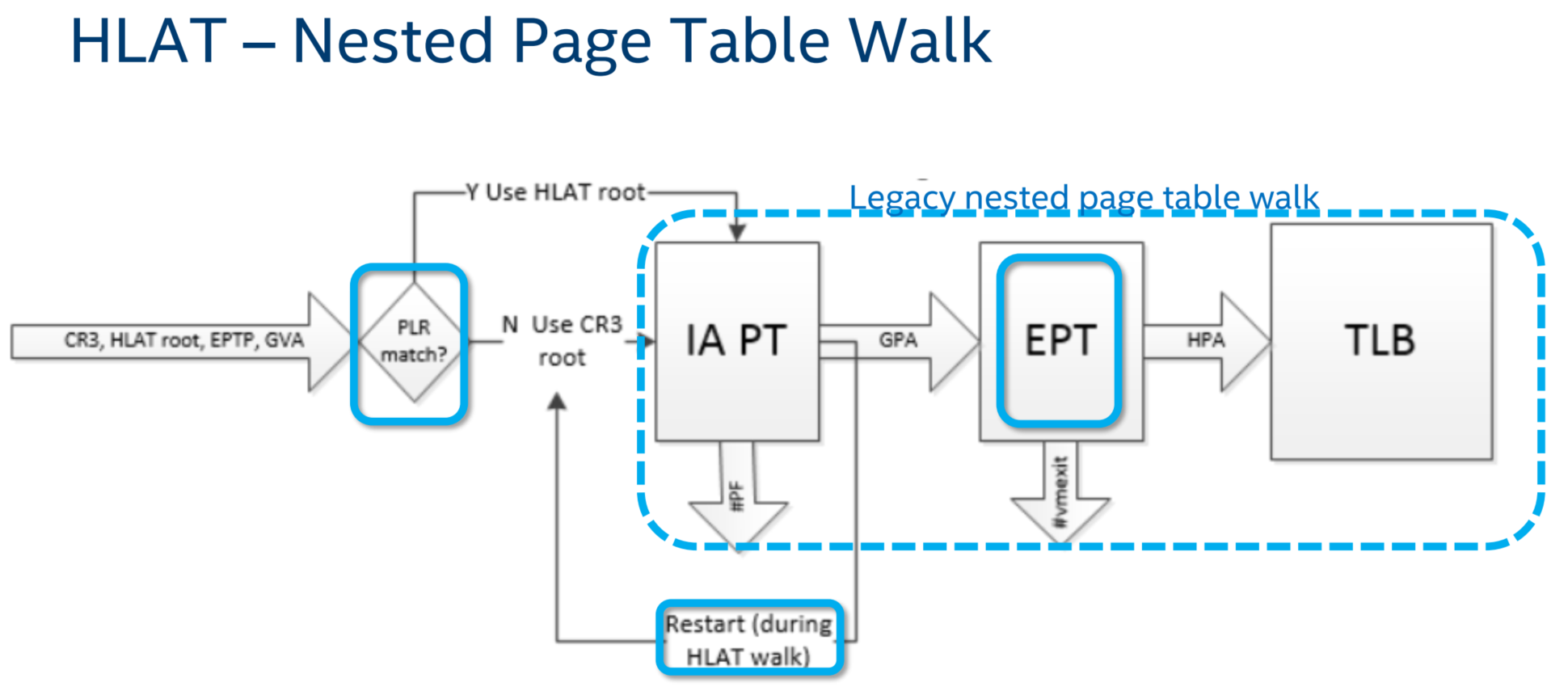
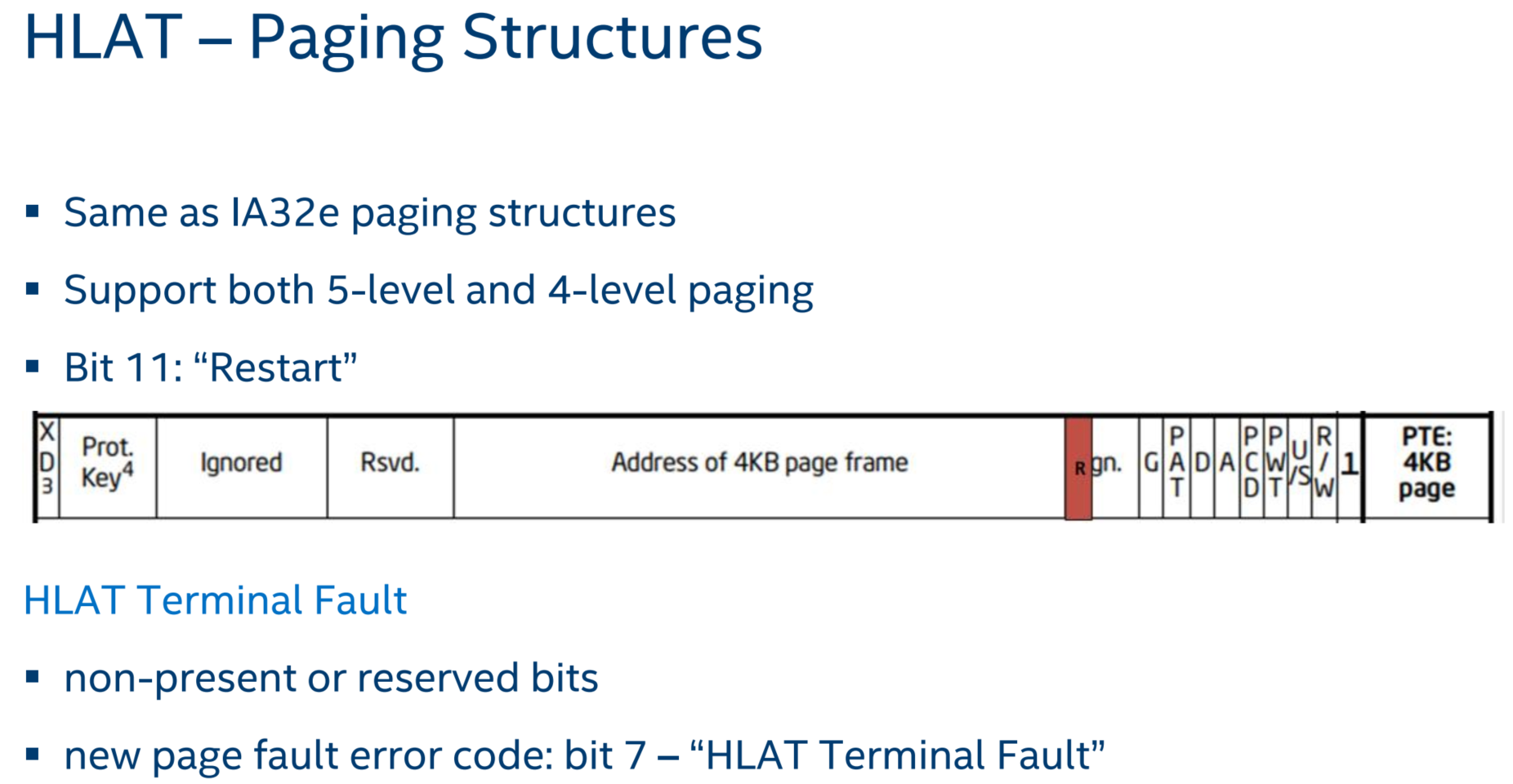
4.2 EPT Control Bit “Paging-Write”
A new EPT control bit called “Paging-Write” specified in EPT leaf entries.


硬件会更新guest paging structure pages的A/D bits without EPT violation VM exits
4.3 EPT Control Bit “Verify Paging-write”
A new EPT control bit called “Verify Paging-Write” specified in EPT leaf entries (that refer to the final host physical page in the translation).
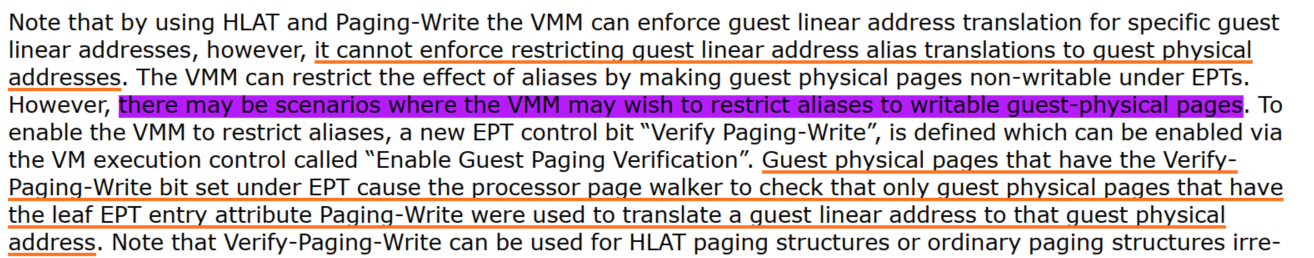
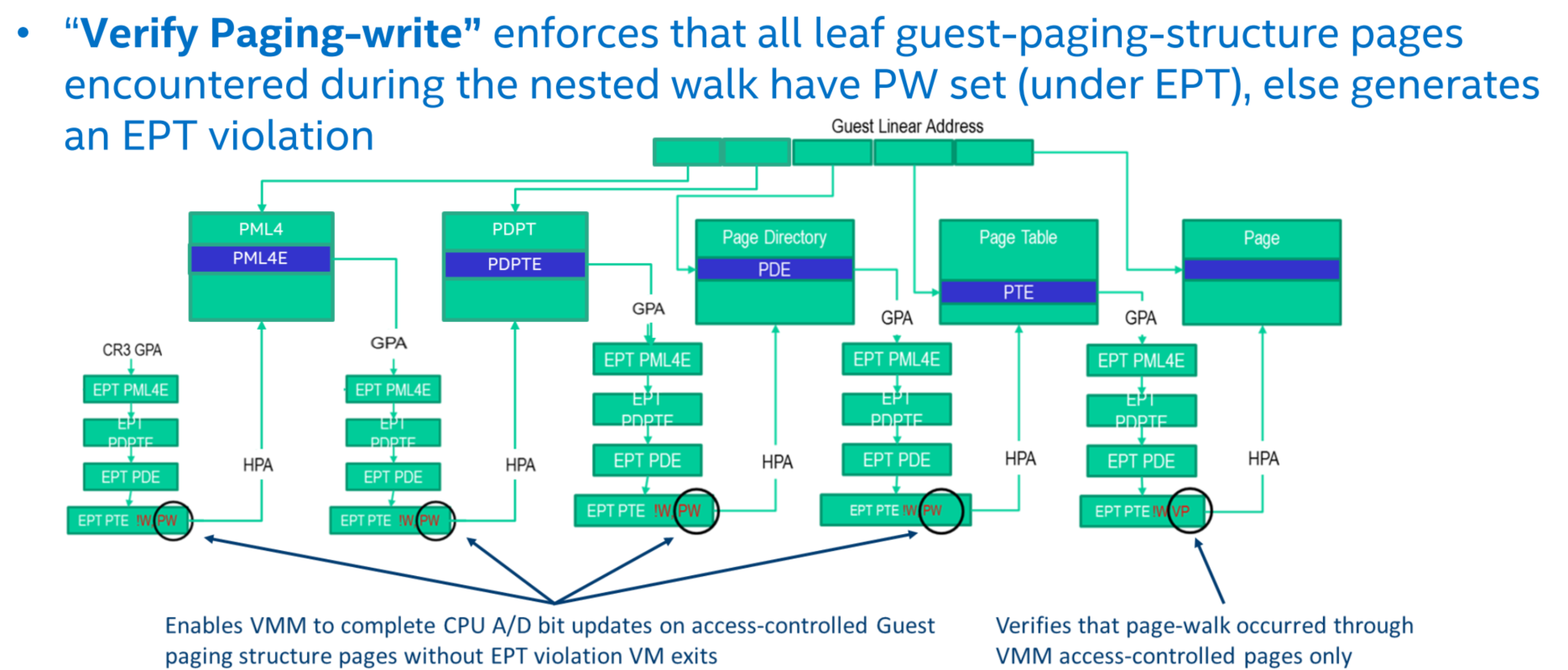
4.4 Prevent Alias Mapping with PW & VPW
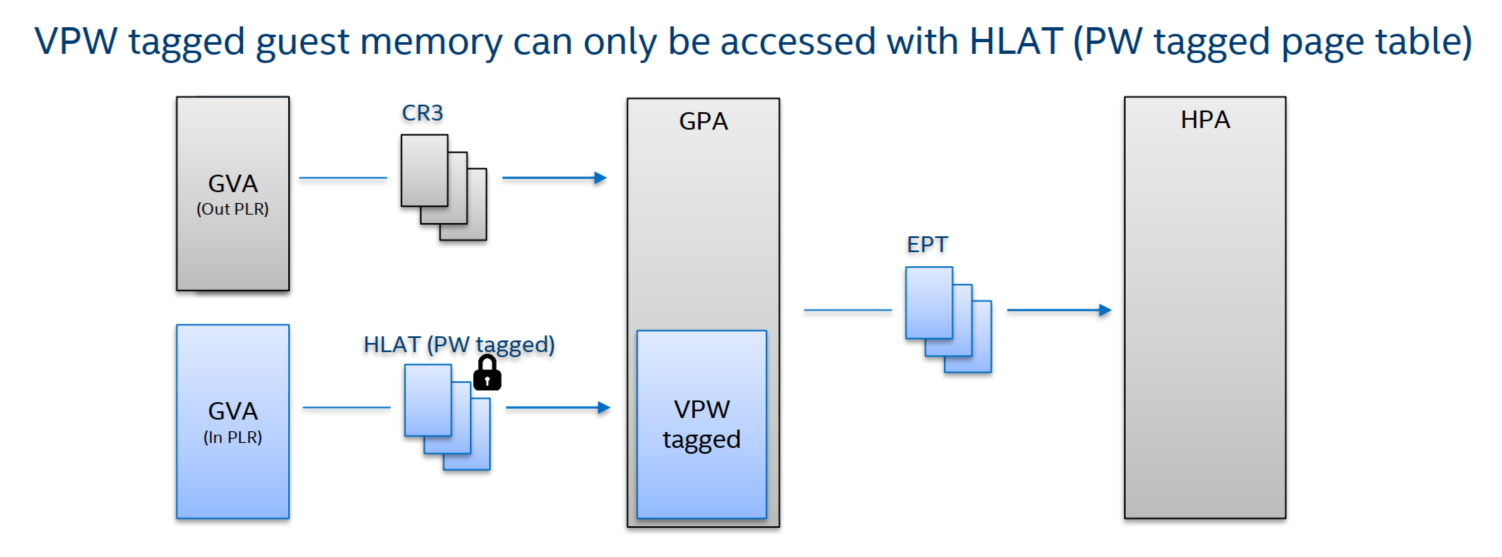
5. Implementaion