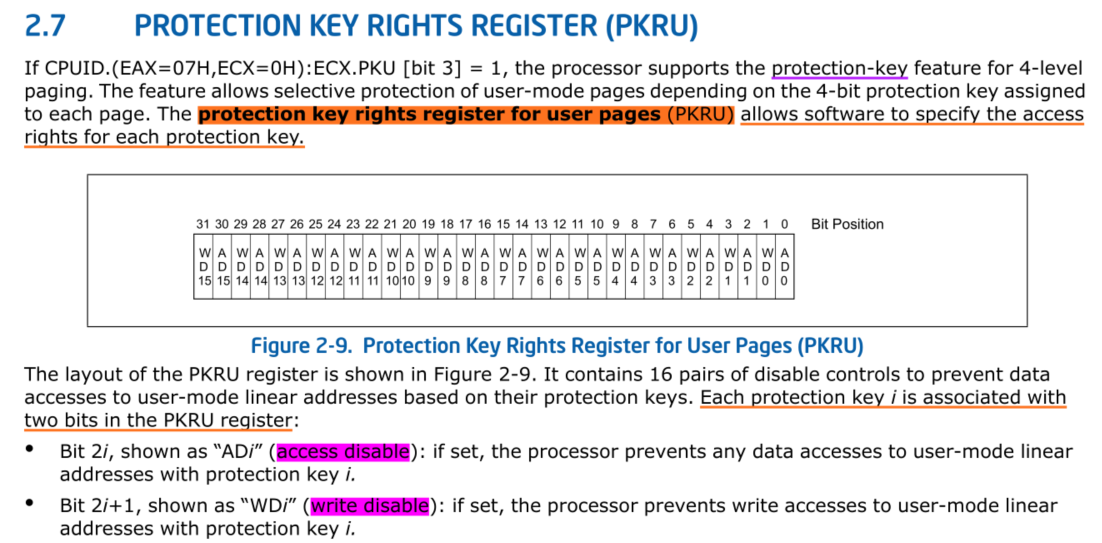
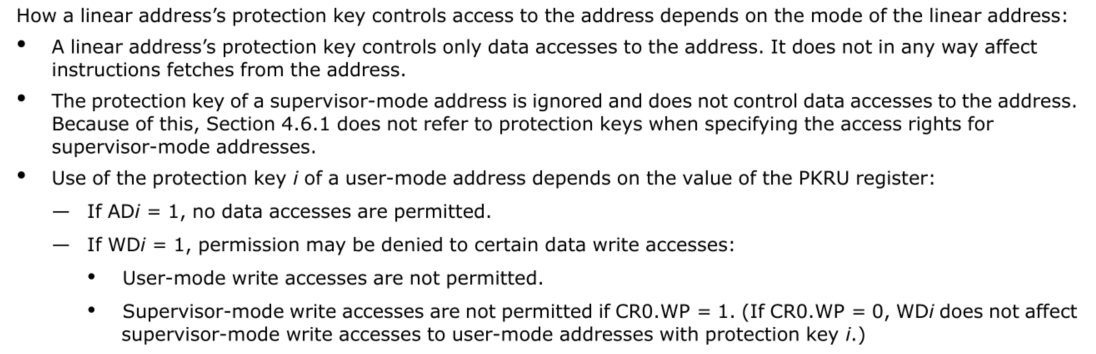
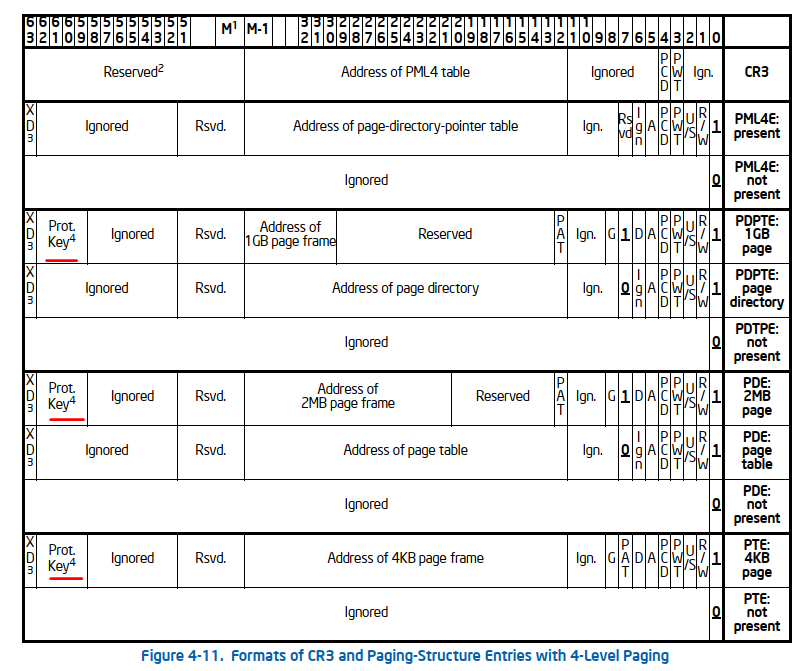
Introduction to PKU
本文将从motivation、usage demo和硬件实现来介绍PKU(Memory Protection Keys for Userspace)。
motivation
Memory Protection Keys (pkeys) are an extension to existing page-based memory permissions. Normal page permissions using page tables require expensive system calls and TLB invalidations when changing permissions. Memory Protection Keys provide a mechanism for changing protections without requiring modification of the page tables on every permission change.
usage demo
To use pkeys, software must first “tag” a page in the page tables with a pkey. After this tag is in place, an application only has to change the contents of a register in order to remove write access, or all access to a tagged page.
1 |
|
The program below allocates a page of memory with read and write permissions. It then writes some data to the memory and successfully reads it back. After that, it attempts to allocate a protection key and disallows access to the page by using the WRPKRU instruction. It then tries to access the page, which we now expect to cause a fatal signal to the application.1
2
3
4$ ./a.out
buffer contains: 73
about to read buffer again...
Segmentation fault (core dumped)
硬件实现
PKU的底层实现依赖于protection key rights register for user pages (PKRU) 。
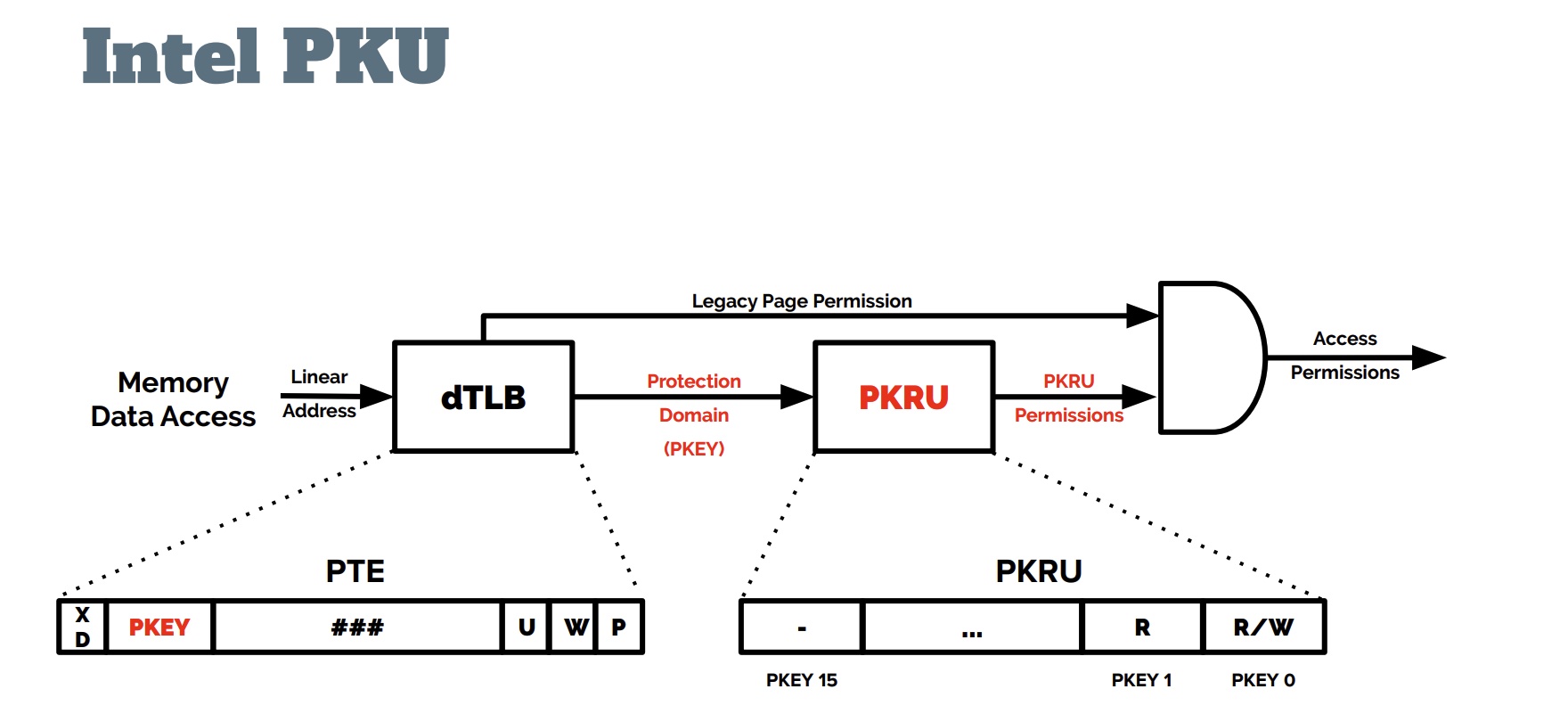
参考资料: