Notes about MBEC(Mode Based Execution Control)
文章目录
本文将mark下MBEC(Mode Based Execution Control)相关notes。
Introduction
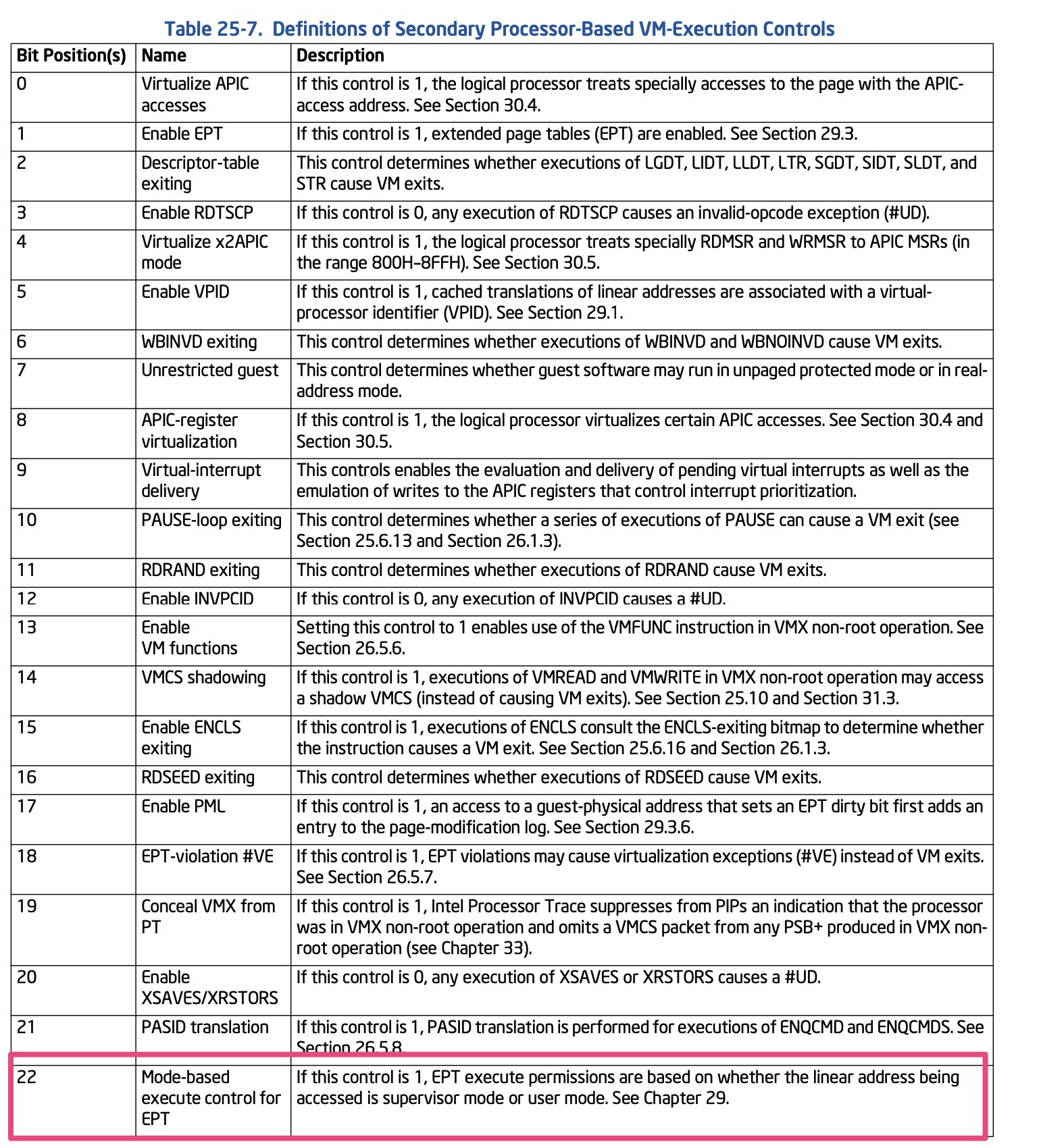
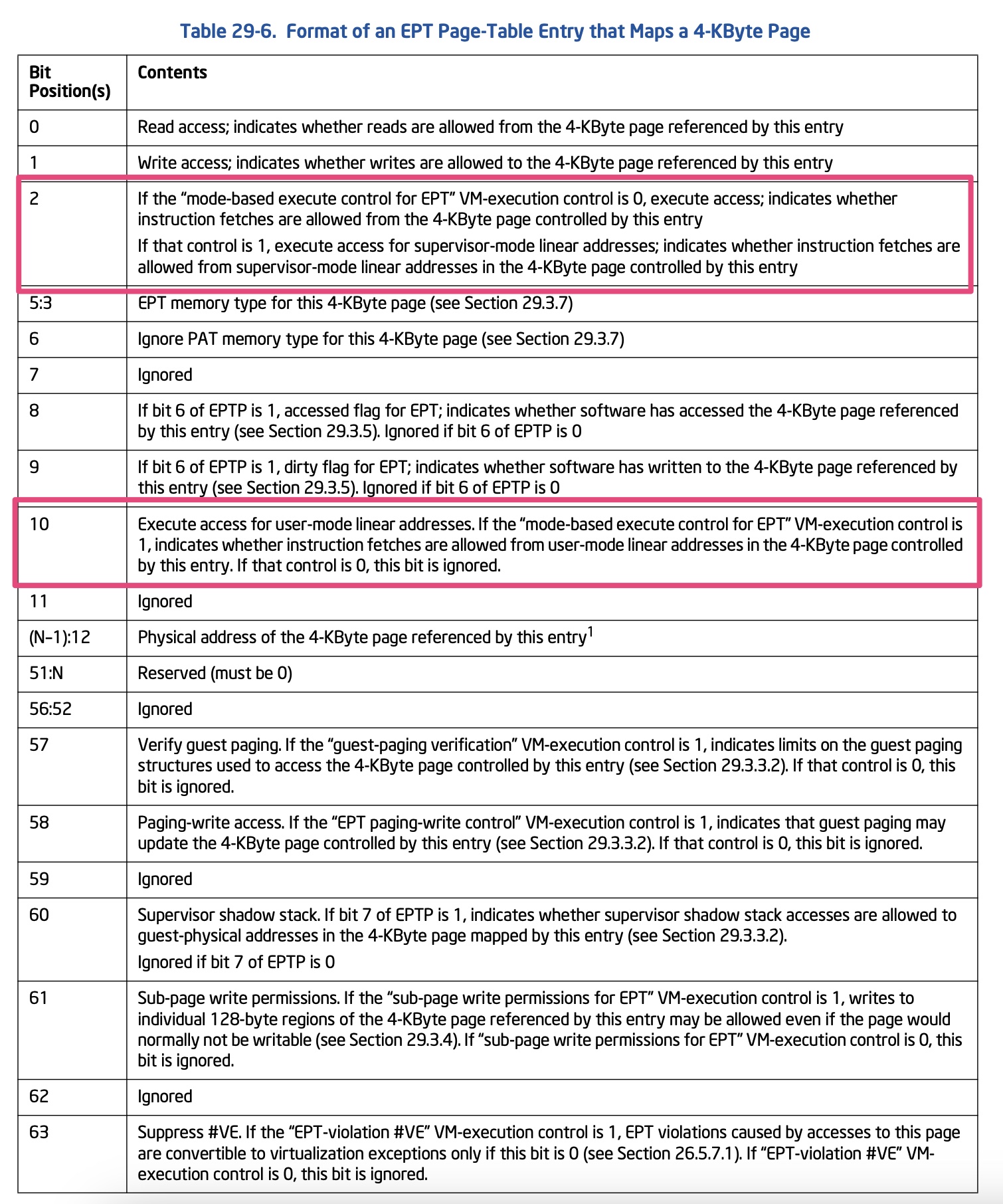
MBEC provides finer grain control on execute permissions to help protect the integrity of the system code from malicious changes. It provides additional refinement within the Extended Page Tables (EPT) by turning the Execute Enable (X) permission bit into two options:
- XU for user pages
- XS for supervisor pages
The CPU selects one or the other based on permission of the guest page and maintains an invariant for every page that does not allow it to be writable and supervisor-executable at the same time. A benefit of this feature is that a hypervisor can more reliably verify and enforce the integrity of kernel-level code(hypervisor可以更可靠地验证和执行内核级代码的完整性). The value of the XU/XS bits is delivered through the hypervisor, so hypervisor support is necessary.
这个特性主要是安全方面的考虑,如果想了解安全相关的更多背景,可以参考Analysis of the Attack Surface of Windows 10 Virtualization-based Security。本文主要侧重于虚拟化侧的内容,安全相关的细节,不在本文的范围之内。
Details
参考资料: