Notes about linux KPTI
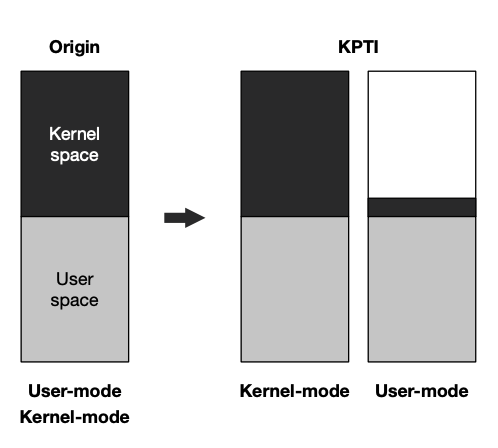
KPTI (kernel page table isolation) is proposed to defend against the Meltdown attack. This patch separates user space and kernel space page tables entirely, as shown in the following figure. The one used by kernel is the same as before, while the one used by application contains a copy of user space and a small set of kernel space mapping with only trampoline code to enter the kernel. Since the data of kernel are no longer mapped in the user space, a malicious application cannot directly de-reference kernel’s data address, and thus cannot issue Meltdown attack.
参考资料:
- EPTI: Efficient Defense against Meltdown Attack for Unpatched VMs(ATC’18)
- https://www.wikiwand.com/en/articles/Kernel_page-table_isolation
- Linux mem 2.3 内核页表隔离 (KPTI) 详解
- Page Table Isolation (PTI)